What Is the SSL DROWN Attack Vulnerability?
The DROWN attack, or Decrypting RSA with Obsolete and Weakened Encryption, is an SSL/TLS vulnerability that allows attackers to decrypt encrypted traffic. It targets servers that still support the outdated SSL 2.0 (SSLv2) protocol and share cryptographic keys between SSLv2 and modern TLS services.
This flaw, which is tracked as CVE-2016-0800, can lead to the exposure of sensitive data, such as your customers’ passwords, personal data, credit card information, and emails.
Despite SSLv2 being deprecated for years, there are still many servers that remain vulnerable due to legacy support or shared certificates across services.
DROWN Attack Impacts: Understanding the CVE-2016-0800 Exploit
CVE-2016-0800 is the public identifier for the SSL DROWN attack vulnerability. Remote attackers can decrypt modern TLS traffic by leveraging weaknesses in SSLv2. In some configurations, decryption takes under a minute.
A system is vulnerable to DROWN if it:
- supports the SSL version 2.0 protocol, directly or indirectly.
- shares RSA private keys across SSLv2 and TLS protocols.
An attacker exploits this setup by making SSLv2 connections to extract key information, which is then used to decrypt TLS-encrypted traffic on the same server. This applies to web servers, email servers, VPNs, and more. It affects services and servers using HTTPS, SMTPS, IMAPS, POP3S, or any SSL/TLS-secured protocol.
Why Is DROWN Still Considered Dangerous?
Although the number of insecure servers has gone down since DROWN was originally found when millions of servers were vulnerable, these flaws remain dangerous to any systems that are not properly secured. (Hint: Don’t be one of them.)
To be a victim of the DROWN attack today is to have sensitive data like passwords, finical data, and emails at risk of being stolen or leaked. In addition to the direct threat of data breaches, organizations subsequently must contend with compliance breaches, reputational damage, and loss of customer trust.
- Exposure: Millions of servers were found vulnerable at the time of discovery. Thankfully, it’s a smaller risk today due to most servers supporting SSL 1.2 as a minimum.
- Fast Attack Time: Data decryption for impacted systems can occur rapidly using optimized techniques.
- Data Breach Risk: Credentials, financial data, and emails can all be exposed.
How to Check Whether Your Site Is Vulnerable to the DROWN Attack
Option 1: Use OpenSSL Commands to Test for SSLv2 (Legacy Systems)
If you’re using and older version of OpenSSL (e.g., OpenSSL 0.9.8), you can test for SSLv2 support on your server using the following command:
openssl s_client -connect yourdomain.com:443 –ssl2 If you’re looking for just a quick check and don’t need as much info, use this command:
openssl s_client -ssl2 -brief -connect yourdomain.com:443If you see an output like “write:errno=104”, it means SSLv2 is off and your server IS NOT vulnerable to the DROWN attack.
In the event of a successful connection, the server is compromised and SSLv2 needs to be disabled at once.
Note: Later versions of OpenSSL (like OpenSSL 3.x) have removed support for the SSLv2 protocol version check entirely and will give an “Unknown option: -ssl2” error. (The same is true for checking protocol versions SSLv3 and TLS1_0.)
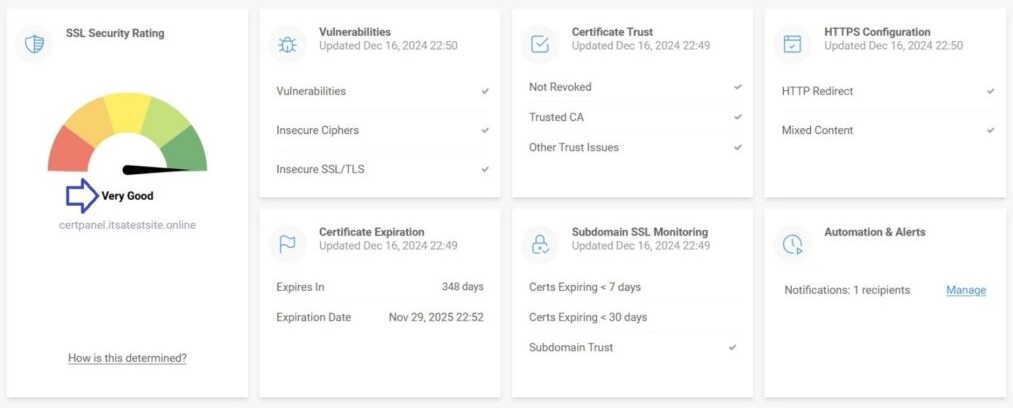
Option 2: Use CertPanel SSL Monitor (Recommended)
Rather than relying on legacy systems, step into the modern age with CertPanel SSL Monitor.
This real-time monitoring tool is ideal for continuous SSL hygiene checks:
- Real-time alerts when outdated protocols are re-enabled.
- Change tracking on cipher suites and protocol updates.
- Actionable reports showing what needs fixing.
Use CertPanel SSL Monitor to check your domain for any SSLv2 and DROWN attack-related issues:
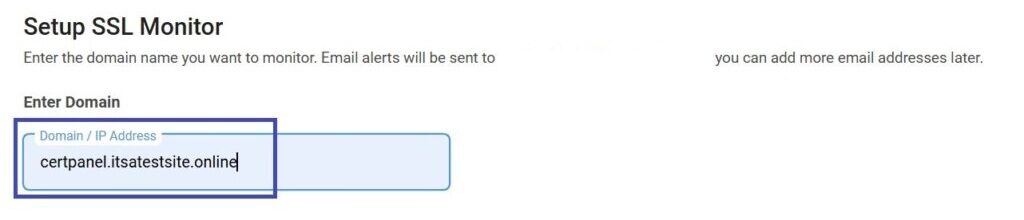
- Add Your Domain:
- Login to your CertPanel account, go to the SSL Monitor feature, input your domain, and click Scan.
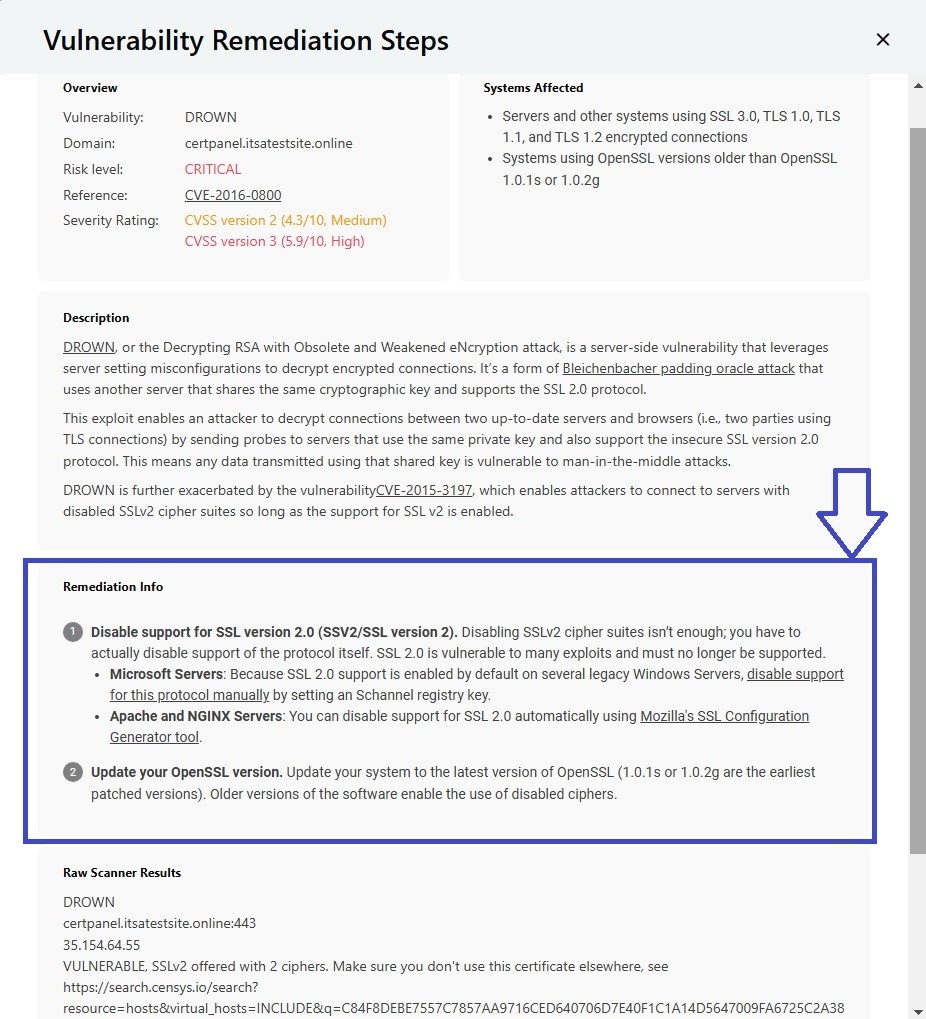
- Analyze Results:
- CertPanel generates a detailed report of your SSL/TLS configurations, including any outdated protocols like SSLv2. It also provides remediation steps to fix the DROWN vulnerability:
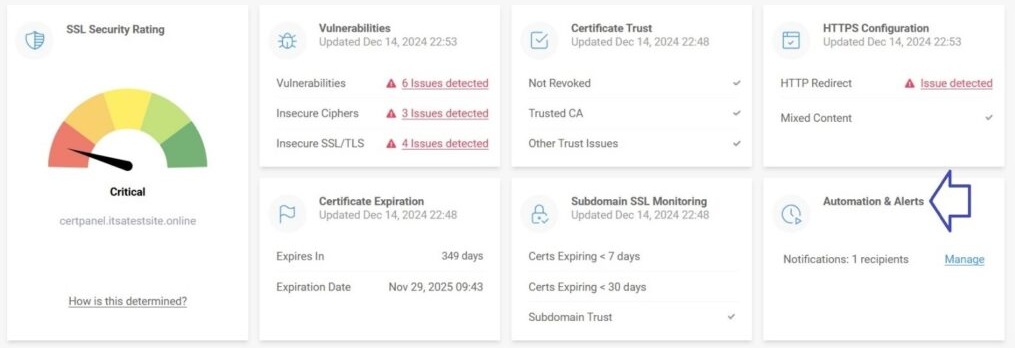
- Set Alerts:
- Enable alerts for outdated protocols or configuration changes to proactively address vulnerabilities.
Here’s a quick peek at how you can use both of these methods:
How to Fix the SSLv2 DROWN Vulnerability in Windows II, NGINX, and Apache
To protect your servers from DROWN attacks, do the following steps for various server environments:
1. Windows Server (IIS)
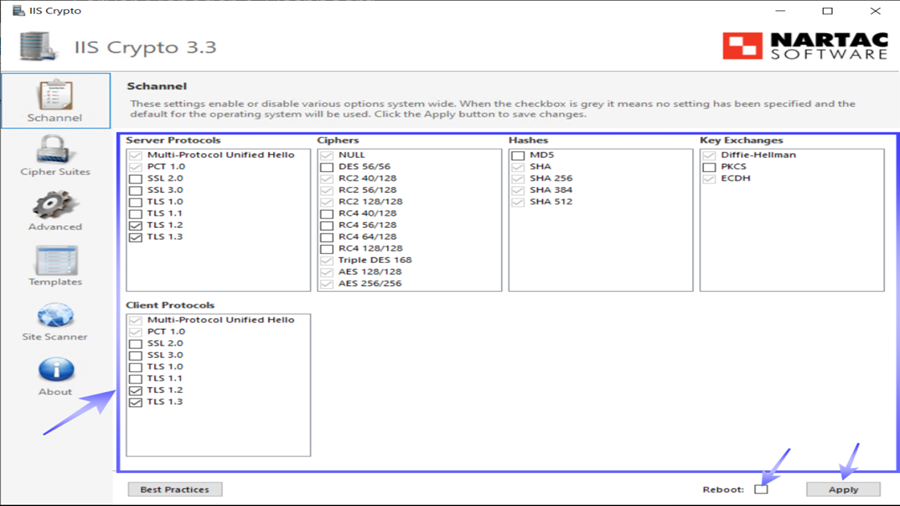
To secure your IIS server from DROWN attacks:
- Download and install IIS Crypto from Nartac Software.
- Open IIS Crypto and select your server.
- Look under Protocols, deselect SSL 2.0, and ensure TLS 1.2 is checked. (You can also turn on TLS 1.3, if your environment supports it.)
- Configure your cipher suites:
- In IIS Crypto Ciphers, deselect all weak ciphers (e.g., RC4), and select only strong ciphers that are compatible with TLS 1.2 or higher.
- Depending on your needs, configure FIPS-compliant ciphers (to meet certain standards).
- Click Apply to apply the changes and reboot the server.
Here’s a quick peek at how this looks:
Restart IIS by entering the following command in a command prompt or PowerShell window:
iisreset Watch the animated walkthrough for fixing the DROWN vulnerability in a Windows IIS Server environment:
2. NGINX
To protect your NGINX server against the DROWN attack:
Edit Your NGINX Configuration File
The exact location of the NGINX configuration file can vary depending on the Linux distribution you are using. For example:
- Ubuntu/Debian:
sudo vim /etc/nginx/sites-available/default
sudo vim /etc/nginx/nginx.conf- CentOS/RHEL/Alma Linux/Rocky:
sudo vim /etc/nginx/conf.d/default.conf
sudo vim /etc/nginx/nginx.confOur example here focuses on Ubuntu/Debian-based systems.
Open the configuration file with:
sudo vim /etc/nginx/sites-available/defaultConfigure Strong Protocols and Ciphers
Add or modify the following lines inside the server block to disable weak protocols and cipher suites, and enforce secure TLS configurations:
# Disable SSLv2 and SSLv3, only allow TLSv1.2 and TLSv1.3
ssl_protocols TLSv1.2 TLSv1.3;
# Specify strong, modern cipher suites
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256';
# Enable Perfect Forward Secrecy (PFS) by using strong key exchange algorithms
ssl_prefer_server_ciphers on;Important Note: NGINX does not support SSLv2. Therefore, it’s not directly vulnerable to the DROWN attack. By explicitly configuring your server to use only modern TLS protocols, you help secure it against vulnerabilities related to outdated SSL/TLS protocol versions.

After making these changes, restart NGINX to apply the configuration:
# sudo systemctl restart nginx Want to see how all of this comes together? Walk through the process with our demo:
3. Apache
To protect your Apache server from the DROWN attack:
Edit Your Apache SSL Configuration File
Start by locating and editing your Apache SSL configuration file. The file path may differ based on your Linux distribution. For example:
- Ubuntu/Debian:
sudo vim /etc/apache2/sites-available/default-ssl.conf- CentOS/RHEL:
sudo vim /etc/httpd/conf.d/ssl.confDisable SSLv2, SSLv3, and Weak Cipher Suites
Add or modify the following lines to disable weak protocols and specify secure cipher suites:
# Disable SSLv2 and SSLv3 to protect against DROWN attacks and other vulnerabilities
SSLProtocol -all +TLSv1.2
# Specify secure cipher suites to avoid including weak ciphers like RC4 and MD5
SSLCipherSuite HIGH:!aNULL:!MD5:!RC4
# Enable strong ciphers and make sure only secure options are used
SSLHonorCipherOrder on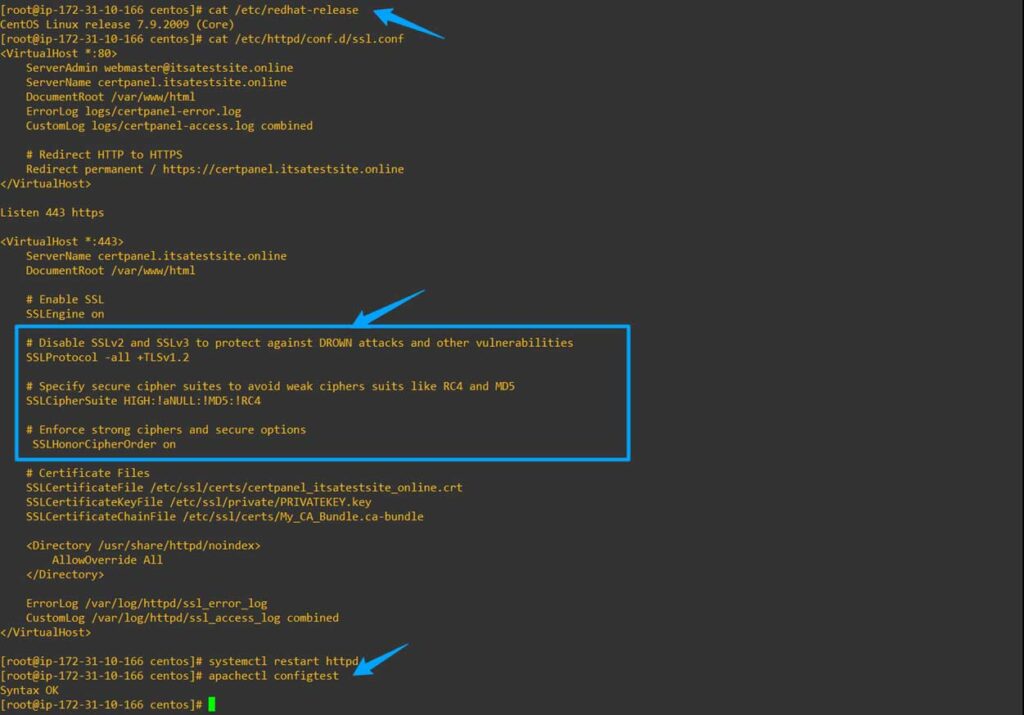
Example:
Our example uses the Ubuntu/Debian distribution. File paths and configuration structure may vary slightly depending on your operating system.
Restart Your Server
After making these changes, restart Apache to apply the new configuration.
For Modern Distros
- Ubuntu/Debian:
sudo systemctl restart apache2- CentOS/RHEL:
sudo systemctl restart httpdFor Older Distros
- Ubuntu or Debian:
sudo service apache2 restart- CentOS/RHEL:
sudo service httpd restartReady to see how everything comes together? Walk through the process now:
Verify Configuration
Your final task is to check whether SSLv2 (and, ideally, all insecure protocol versions) are disabled, and that your server is using strong cipher suites:
- Use an external SSL/TLS testing tool like OpenSSL to confirm that SSLv2 and other weak protocols are disabled, and only secure protocols and ciphers are in use.
- Then use CertPanel SSL Monitor to continuously track SSL/TLS changes and receive proactive alerts for any misconfiguration or regression.
Key Takeaways to Avoid DROWN Attacks
- Disable all legacy protocols: Make sure that SSLv2 is disabled on all servers, as the primary DROWN attack is exploits it.
- Use CertPanel SSL Monitor to keep an eye on your domain and server configurations. For example, CertPanel SSL Monitor automatically:
- detects when servers are still using old and/or wrongly configured SSL protocols
- provides actionable and detailed vulnerability reports to facilitate fast remediation
- offers real-time alerts when there are issues regarding SSL/TLS that must be dealt with quickly.
- Ensure your servers are updated with the latest OpenSSL versions. This will enable you to patch vulnerabilities such as CVE-2016-0800. Regular maintenance prevents exploitation through outdated libraries.
- Enforce modern encryption standards. Replace weak cipher suites with secure ones like TLS 1.2 or higher. Avoid configurations allowing cross-protocol attacks.
- Test your servers regularly: Run periodic scans using CertPanel’s suite of tools to ensure your systems are safe from newly discovered vulnerabilities.
Final Thoughts
The DROWN attack points to the need for security best practices and maintaining SSL/TLS configurations to keep them up to date. Although the SSLv2 protocol is dated, its potential presence within modern server configurations still poses severe risks to vulnerable servers and other systems.
With the use of tools such as CertPanel SSL Monitor, updated servers, and compliance with modern encryption standards, one can protect one’s system from DROWN as well as other similar vulnerabilities.
FAQs
A: The CertPanel’s SSL Monitor offers real-time scanning with detailed reports on SSL/TLS configurations to help detect such vulnerabilities as the DROWN attack and raise alerts for misconfigurations for prompt action.
A: Disabling SSLv2 is a good starting point, but you need to update OpenSSL libraries and force strong cipher suites for all connections for complete protection.