SSL/TLS protocol session renegotiation allows a client and server to update cryptographic parameters during an active session using a new handshake. Renegotiation in SSL is traditionally initiated by the server (i.e., server-initiated renegotiation), but it also can be initiated by the client (i.e., client-initiated renegotiation).
While this legitimate SSL/TLS handshake function adds flexibility to a session, it also can be exploited in what’s known as SSL renegotiation attacks. This SSL renegotiation vulnerability can be exploited by a so-called “man-in-the-middle (MitM)” attack, which can lead to session hijacking, both of which pose serious security risks:
- Man-in-the-Middle (MitM): The attacker intercepts data in transit and possibly injects data without completely taking over the session.
- Session Hijacking: The attacker takes control of an active session, impersonating the user and replacing them in the session altogether.
In this article, we’ll discuss
- what the SSL/TLS protocol session renegotiation security vulnerability is,
- an overview of how an SSL renegotiation attack works,
- how to check for this issue (and other vulnerabilities) using CertPanel SSL Monitor, and
- mitigation strategies to secure your website against the SSL renegotiation vulnerability.
What Is an SSL Renegotiation Attack?
An SSL renegotiation attack, also known as a TLS renegotiation attack, is an exploit that targets vulnerabilities in the renegotiation processes of older versions of the SSL and TLS security protocol handshakes. Attackers may force a renegotiation to inject malicious data into an ongoing session or delay cryptographic verification to manipulate secure communications.
Common Variants of Attack:
- Insecure Client-Initiated Renegotiation: Allows attackers to overwhelm a server’s resources, leading to denial of service (DoS) attacks.
- Renegotiation Injection Attack: Enables attackers to inject unauthorized requests, resulting in partial session hijacking.
- SSL Triple Handshake Vulnerability: CVE-2015-6112 allows an attacker to exploit separate vulnerabilities to link two sessions impersonating the client.
Note: These attack types may involve MitM data interception or escalate into full session hijacking.
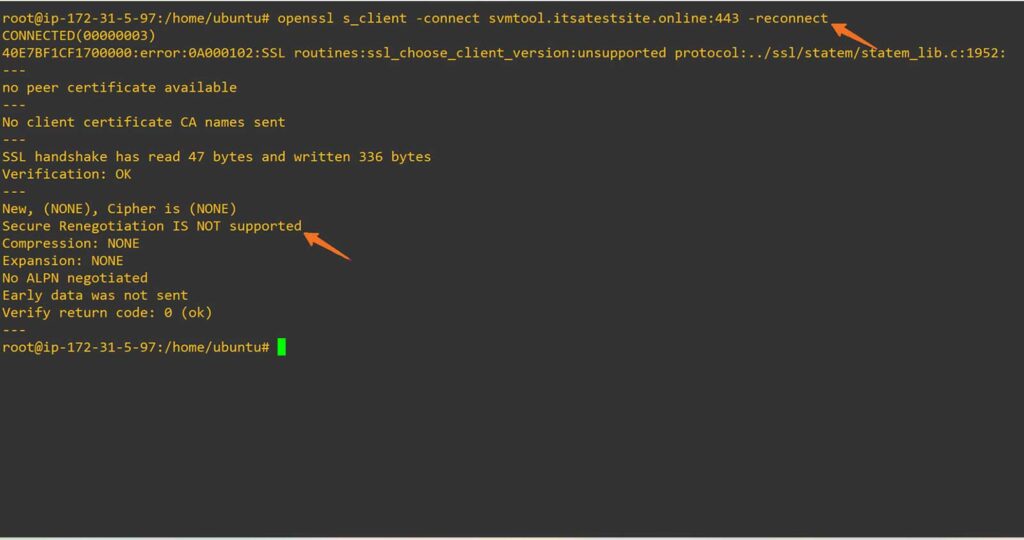
Note: Insecure renegotiation vulnerabilities typically do not trigger browser-visible error messages. Instead, you need to check the server’s renegotiation support directly via OpenSSL commands.
On modern Ubuntu version, running this command:
# openssl s_client –connect yourdomain.tld:443 –reconnectOf course, you’ll replace the generic “yourdomain.tld” info with your actual domain information. Using our test domain as an example, here’s how this would look:
# openssl s_client -connect svmtool.itsatestsite.online:443 -reconnectHow to Detect SSL Renegotiation Vulnerability
Step 1: Test for Renegotiation Support Using OpenSSL Command
Use OpenSSL’s reconnect features to test for secure or insecure renegotiation support using the command we covered moments ago:
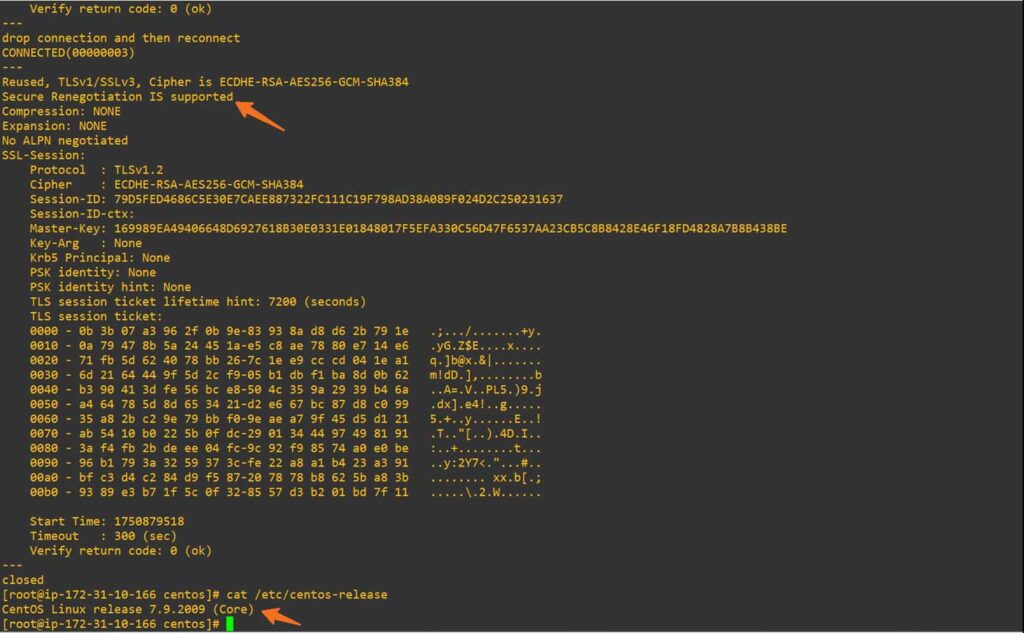
# openssl s_client -connect yourdomain.tld:443 -reconnectNote: Some resources mention pressing the R key after connecting with OpenSSL to initiate renegotiation. However, in both modern systems (like Ubuntu 22) and legacy systems (like CentOS 4), the -reconnect flag triggers renegotiation automatically. No manual input (i.e., typing R) was required during our testing.
Check for output:
- Secure Renegotiation IS supported = Secure
- Secure Renegotiation IS NOT supported = Not secure and vulnerable
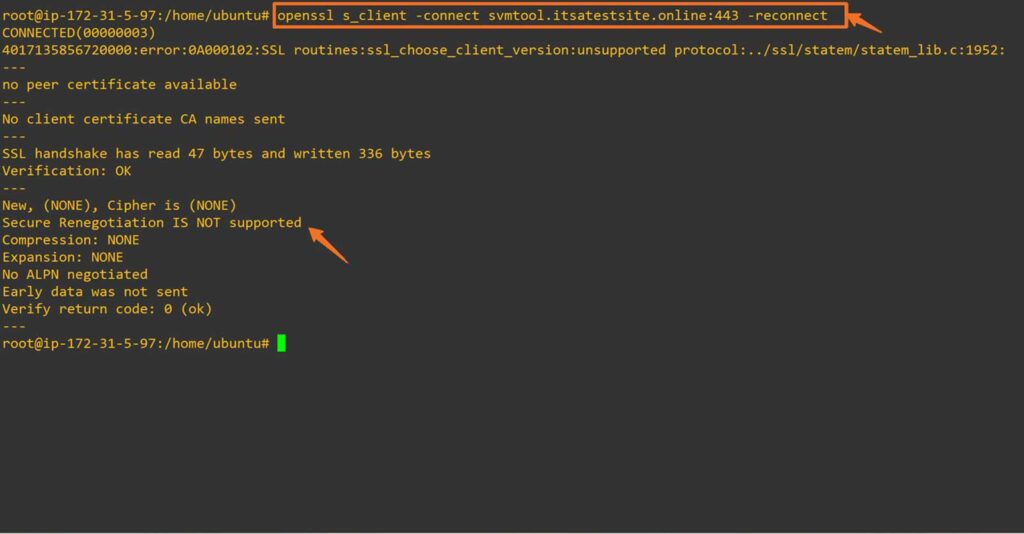
So, what would you see on modern systems? On servers that support TLS 1.3, you’ll see an output like this instead:
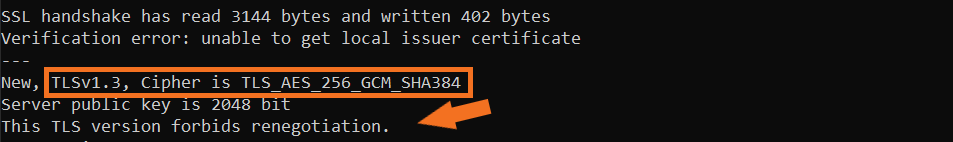
This type of output appears only on systems that support TLS 1.3 and recent OpenSSL versions. This is because TLS 1.3 doesn’t support renegotiation.
Note: If you’re testing on older systems like CentOS 4 or 5, you won’t see this message because they don’t support TLS 1.3 or modern cipher protocols. The output shown above reflects the expected behaviour on secure, up-to-date servers.
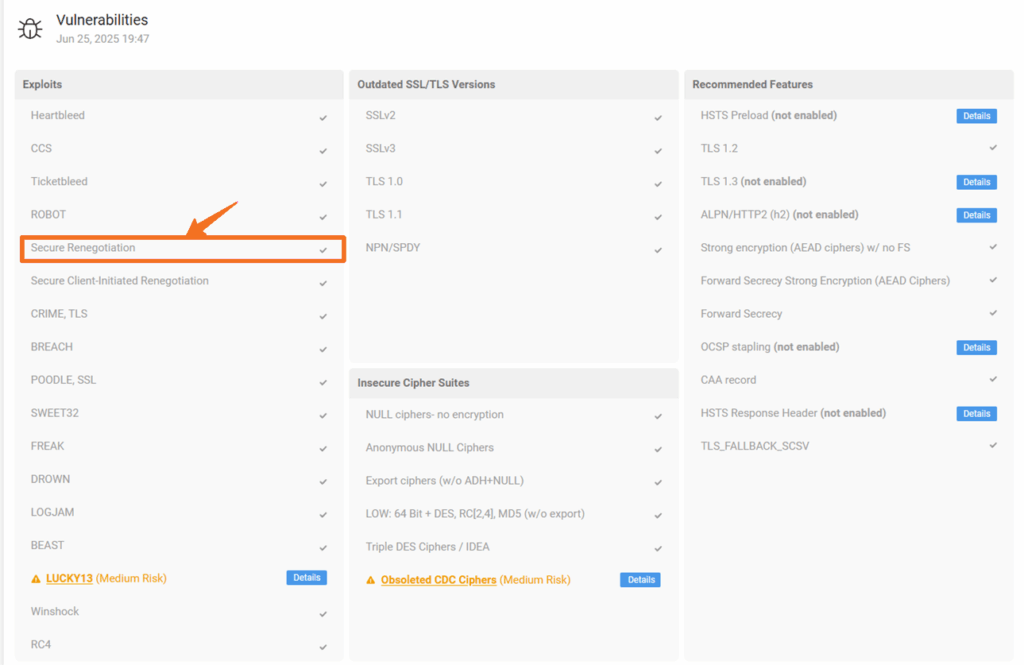
Step 2: Verify Your Server’s Renegotiation Status with CertPanel SSL Monitor
For continuous monitoring and detailed insights, use CertPanel SSL Monitor.
- Log in to your CertPanel account.
- Navigate to the SSL Monitor section.
- Enter your domain and initiate the scan.
- Review the Renegotiation Supported status.
Check out this demo that shows how to detect SSL renegotiation vulnerabilities using CertPanel SSL Monitor:
How to Fix SSL Renegotiation Vulnerability
Note: This guide covers fixing SSL/TLS renegotiation issues for Apache and NGINX servers. If you’re using Microsoft IIS (version 6 or newer), you don’t need to worry about this — IIS doesn’t allow insecure client-initiated renegotiation.
1. Disable Insecure Renegotiation and Configure Secure Ciphers Suites
Protect your server by disabling insecure renegotiation and configuring strong encryption methods in its SSL configuration file.
For Apache on CentOS/RHEL
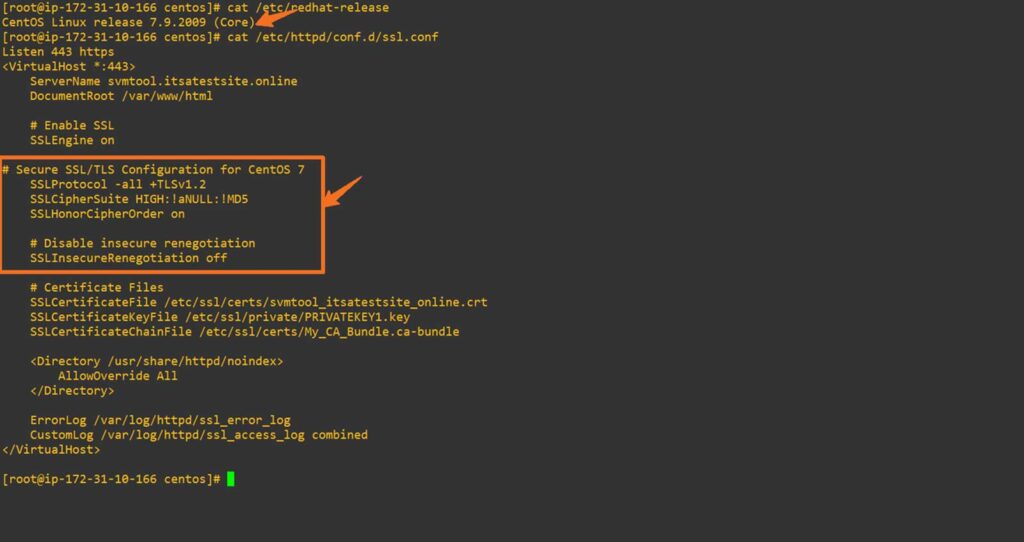
File Path: /etc/httpd/conf.d/ssl.conf
Add or update the following directives to use TLS 1.2 as a minimum, so long as it’s properly configured. (Ideally, use TLS 1.3 since that version of the protocol eliminates renegotiation entirely.):
# Secure SSL/TLS Configuration for CentOS 7
SSLProtocol -all +TLSv1.2
SSLCipherSuite HIGH:!aNULL:!MD5
SSLHonorCipherOrder on
# Enforce Secure Renegotiation
SSLInsecureRenegotiation offNote: TLS 1.3 eliminates renegotiation entirely by design. However, CentOS 7 does not support TLS 1.3 with its default OpenSSL version. To fully eliminate renegotiation, consider upgrading to a system that supports TLS 1.3.
Test and Restart Apache
# apachectl configtest # Check for syntax errors in Apache configuration
# service httpd restart # For older systems like CentOS 5 or 6
# systemctl restart httpd # For newer systems like CentOS 7 or laterFor NGINX on Ubuntu/Debian
Note: In modern Ubuntu versions like 22.04, insecure renegotiation is already disabled by default (OpenSSL 1.1.1 release notes) and cannot be re-enabled. Therefore, this section demonstrates secure configuration best practices, not vulnerability remediation. Older Ubuntu versions (e.g., 10.04) do not support TLS 1.2/1.3 or renegotiation control options, and are not suitable for mitigation.
File Path: /etc/nginx/sites-available/default
Update the SSL settings as follows to ensure the use of secure protocols (ideally, TLS 1.3) and cipher suites:
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;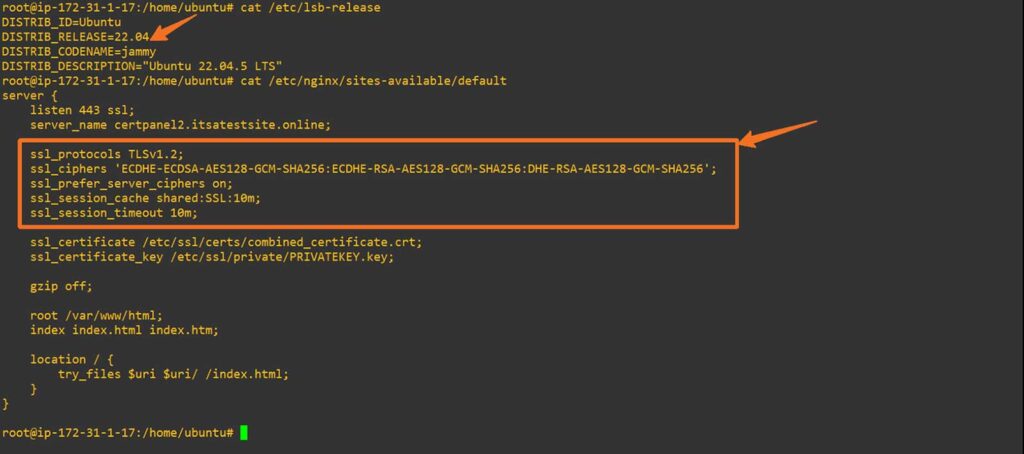
Note: TLS 1.3 disables renegotiation entirely by design. If your server and clients support it (as with modern Ubuntu versions), enabling TLS 1.3 is the most secure approach and avoids renegotiation-related vulnerabilities altogether.
Test and Restart NGINX
# nginx -t # Check for syntax errors in NGINX configuration
# service nginx restart # For older Ubuntu systems using SysVinit
# systemctl restart nginx # For newer Ubuntu systems using systemd2. Upgrade OpenSSL to a Secure Version
While SSL/TLS renegotiation flaws originate at the protocol level, whether a server is vulnerable depends on how its SSL/TLS library (e.g., OpenSSL) implements those rules. Earlier versions of OpenSSL, especially those released before 1.0.1g, didn’t fully support secure renegotiation as outlined in RFC 5746. As a result, servers running outdated versions remained exposed even after the protocol fix.
Updating to a modern OpenSSL version ensures that renegotiation is either securely handled or entirely disabled, depending on what’s supported.
Ensure that you are using OpenSSL version ≥ 1.0.1g to avoid SSL renegotiation attacks.
For Modern Distributions (Ubuntu/CentOS)
Use the following commands to install an update for OpenSSL:
# sudo apt update && sudo apt install openssl
# sudo openssl versionFor Older Distributions
You must compile and install OpenSSL manually using the following commands:
# wget https://www.openssl.org/source/openssl-1.0.1g.tar.gz
# tar -xzf openssl-1.0.1g.tar.gz
# cd openssl-1.0.1g
# ./config
# make
# sudo make install
# sudo openssl version
# sudo find / -name openssl
# sudo mv /usr/bin/openssl /usr/bin/openssl.old
# sudo ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
# sudo openssl versionConfirm the Fix Worked
Once you’ve applied the fix on your server, it’s important to test whether your server is now secure.
- Re-run openssl s_client -connect yourdomain.com:443 -reconnect
- Use CertPanel SSL Monitor again and verify your domain’s renegotiation status:
Secure Renegotiation: Enabled (Secure) OR Disabled
Keep Your Server Safe and Secure
SSL renegotiation attacks pose significant threats to server security, potentially leading to DoS attacks and other serious threats. By disabling insecure renegotiation, configuring strong cipher suites, using a secure version of OpenSSL, and implementing rate limiting, you can protect your website from these vulnerabilities.
For continuous security and monitoring, use CertPanel SSL Monitor, which can detect and fix SSL/TLS vulnerabilities in real time.
Interactive Demo: See How to Fix SSL Renegotiation Vulnerabilities
Watch the animated walkthrough for fixing SSL renegotiation vulnerabilities in Apache on CentOS/RedHat.
- Update the Apache SSL configuration
- Disable insecure renegotiation
- Restart Apache and validate using OpenSSL & CertPanel SSL Monitor.
Note: Fixes are demonstrated on CentOS because insecure renegotiation cannot be re-enabled in modern Ubuntu NGINX environments.