In many ways, proper SSL vulnerability management is primarily about staying abreast of the latest technologies and best practices. By identifying weaknesses in those technologies (e.g., SSL and TLS protocols) and the ways they’re managed, you can help mitigate the risks that cybercriminals love to exploit.
As such, SSL vulnerabilities are crucial to monitor because they lead to security breaches that reveal confidential information and devastate consumer trust in your brand. That’s why there’s a growing number of tools (e.g., SSL vulnerability scanners) and setups that can help handle the management workload and mitigate downtime.
In this article:
- explore the most common SSL/TLS vulnerabilities,
- discuss best practices for managing them, and
- introduce CertPanel SSL Scanner, a powerful tool for SSL vulnerability management.
- provide practical examples of securing various server environments, including
- Amazon Linux with Apache,
- Ubuntu with NGINX, and
- Windows Server with IIS.
What Are SSL Vulnerabilities?
SSL vulnerabilities represent weaknesses in the implementation of the secure sockets layer (SSL)/transport layer security (TLS) protocols, configurations of the server, or the management of certificates that can be exploited by an attacker.
Examples of the most common SSL vulnerabilities include:
- Outdated Protocols: Use of obsolete security protocol versions like SSL 3.0 or older versions of TLS.
- Weak Cipher Suites: Cipher suites with low encryption strength or vulnerable to attacks like BEAST or FREAK.
- Certificate Problems: Expired, self-signed, or improperly configured SSL certificates.
- Misconfigurations: Failure to enforce HTTPS or incorrect server settings.
If your website doesn’t have SSL/TLS encryption enabled, then here’s a quick look at what your visitors will see when they try to access it:
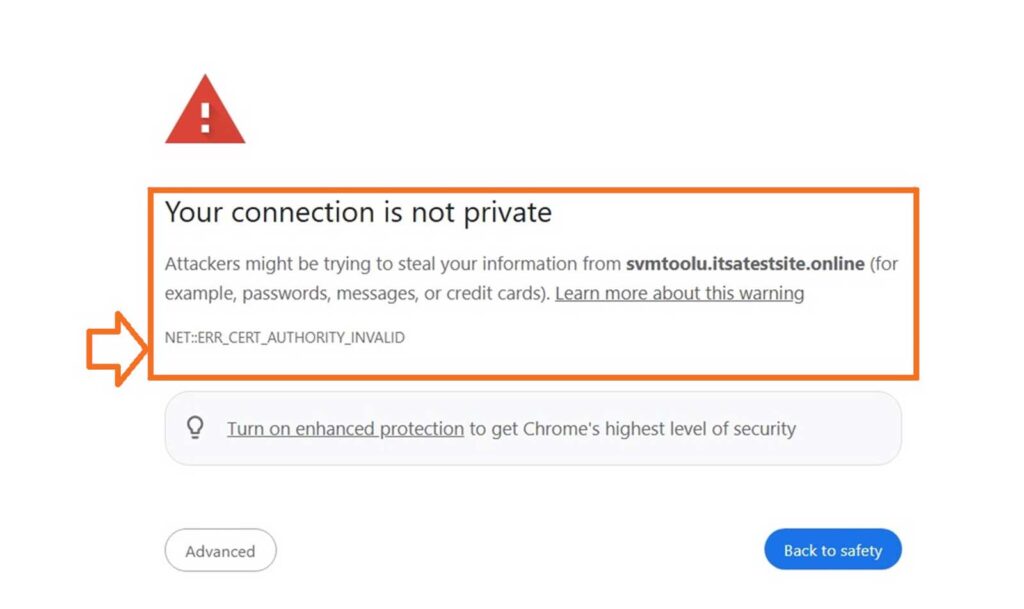
Importance of SSL Vulnerability Management
SSL vulnerabilities, if not adequately addressed, can cause devastating consequences that affect businesses. These direct and indirect impacts also touch businesses’ partners, customers, and other individuals and entities. Some examples of such consequences include:
- Data Breaches: SSL vulnerabilities enable attackers to easily intercept sensitive passwords, credit cards, and any other personal details.
- Incident Response and Remediation Costs: The costs of addressing exploited SSL vulnerabilities are growing by the day. But there are additional costs that you may not be considering, such as legal
- SEO Ranking Losses: Google penalizes insecure websites that display SSL vulnerability-related warnings such as “Your connection is not private” and “Warning: Potential Security Risk Ahead” in users’ browsers.
- Customer Trust: Even just seeing a message indicating that a site is insecure can be enough to drive prospective customers into competitors’ arms. (And God forbid there’s a resulting cybersecurity incident — that can deal a devastating blow to the organization’s reputation.)
- Heavy Regulatory Penalties: Non-compliance with industry or geographic data privacy and security regulations, such as the European Union’s General Data Protection Regulation (GDPR), can lead to heavy fines and penalties.
Effective SSL vulnerability management ensures your server configurations are robust, your certificates are up to date, and your site is resilient to attacks.
How to Identify SSL Vulnerabilities: Use an SSL Vulnerability Scanner
Finding SSL vulnerabilities doesn’t have to be a major undertaking.
CertPanel SSL Scanner Simplifies Vulnerability Management
The process of identifying SSL vulnerabilities has been simplified through CertPanel SSL Scanner. The tool scans your website and flags 110+ weaknesses, such as cipher suites, expired certificates, and protocol-based flaws.
This SSL scan online tool is part of CertPanel’s SSL Monitor feature. The detailed scan report component identifies the areas that need correction and provides recommendations with actionable improvements.
How to Check for SSL Vulnerabilities Using CertPanel’s SSL Scan Online Tool
- Log in to your CertPanel account. In the main dashboard, scroll down to the Featured Products section and click Activate SSL Monitor. On the next page, enter your domain/IP address in the Setup SSL Monitor field and complete the payment information to use the feature’s SSL scan online tool.

- Click Initiate Scan to start the SSL/TLS vulnerability scan for the specified domain/IP address. NOTE: The scan will take a few minutes. So, take the time to grab a cup of coffee or love on your pet(s) (for you work-from-home types).
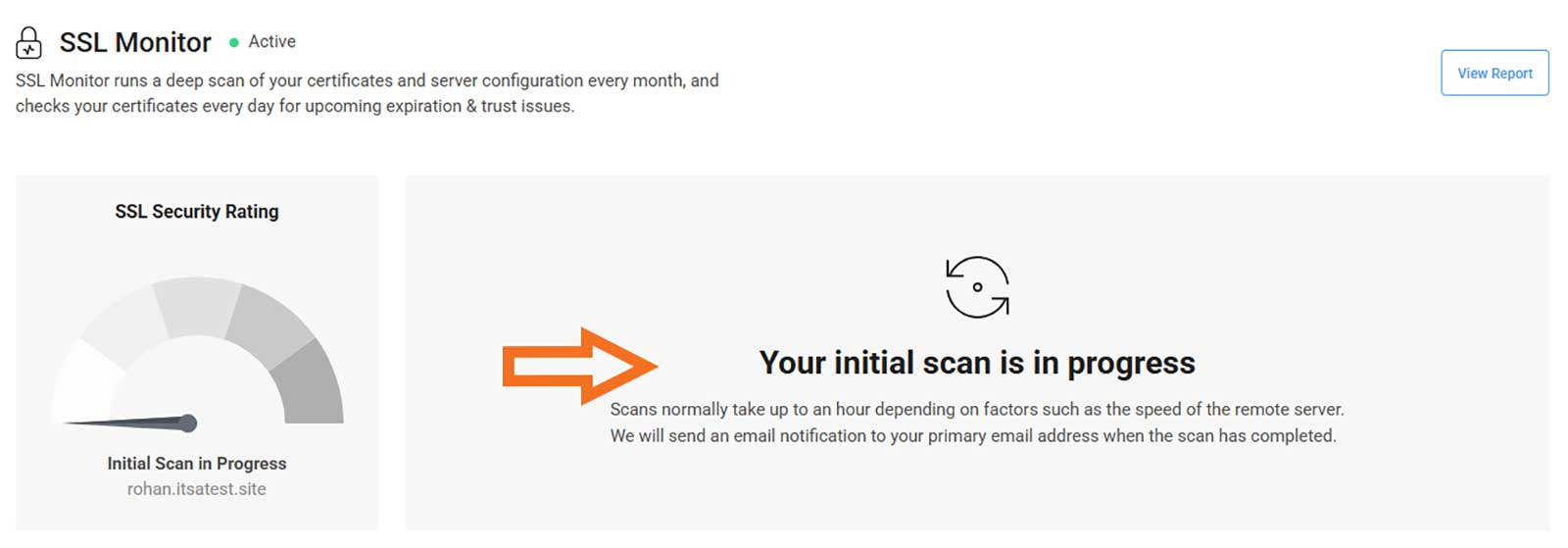
- Once the scan is complete, select View Report to access the detailed report to learn which vulnerabilities are present.

See any items that have a clickable Details button instead of a checkmark? Be sure to click on it to learn what steps you can take to safeguard your website against each possible threat.
It really is that simple with SSL Monitor’s online SSL vulnerability scanner + remediations!
Best Practices for SSL Vulnerability Management
- Update Your Server’s SSL/TLS Protocols
- Make sure your server supports only the latest versions of TLS (e.g., TLS 1.2 or 1.3).
- Disable old protocols such as SSL 3.0 and TLS 1.0/1.1.
- Use Only Strong Cipher Suites
- Configure your server to use secure and recommended industry-standard cipher suites.
- Disable weak ciphers such as RC4 and DES.
- Renew and Validate SSL Certificates
- Monitor your SSL/TLS certificates for expiration.
- Use a reputable CA to issue certificates.
- Enable HTTP Strict Transport Security (HSTS)
- Enforce HTTPS by implementing HSTS headers to prevent man-in-the-middle (MITM) attacks.
- Make Automation Work for You with CertPanel
- Having expired SSL/TLS certificates on your site can be avoided with CertPanel AutoInstall SSL.
- Use tools like CertPanel SSL Monitor to schedule regular scans and receive alerts for vulnerabilities.
Secure Your Server Using Server-Specific Configurations
1. Amazon Linux with Apache
- Update OpenSSL and Apache:
sudo yum update openssl httpd - Enable strong cipher suites:
Edit the SSL configuration file located at the following file path:
sudo vim /etc/httpd/conf.d/ssl.conf Add the following settings to the config file:
# Protocols - Use Only TLS 1.2
SSLProtocol -all +TLSv1.2
# Updated Cipher Suites - Exclude Weak Ciphers
SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:!CBC:!RC4:!SHA1:!3DES:!MD5:!LOW:!EXP:!aNULL:!eNULL
SSLHonorCipherOrder On 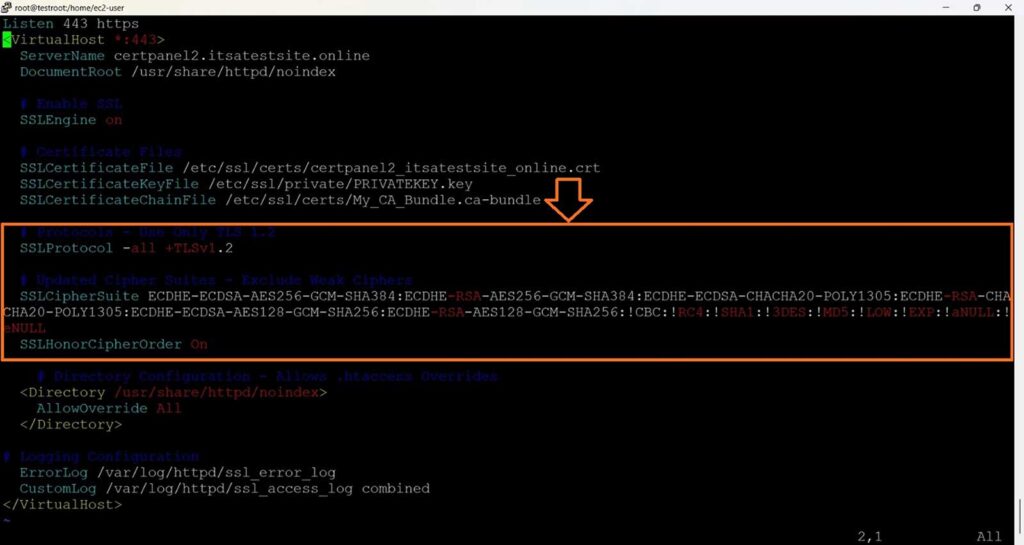
- Restart your Apache server:
sudo systemctl restart httpd 2. Ubuntu with NGINX
- Update OpenSSL and NGINX:
sudo apt-get update && sudo apt-get install openssl nginx - Configure strong SSL settings: Edit the NGINX configuration file, which is located at the following file path:
sudo vim /etc/nginx/sites-available/default - Specify the following secure protocols and ciphers under the server block:
# Add SSL protocols and ciphers for stronger security (adjust as needed)
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256';
# Disable HTTP data compression (GZip/Deflate) to mitigate BREACH attacks.
gzip off;
ssl_prefer_server_ciphers on; 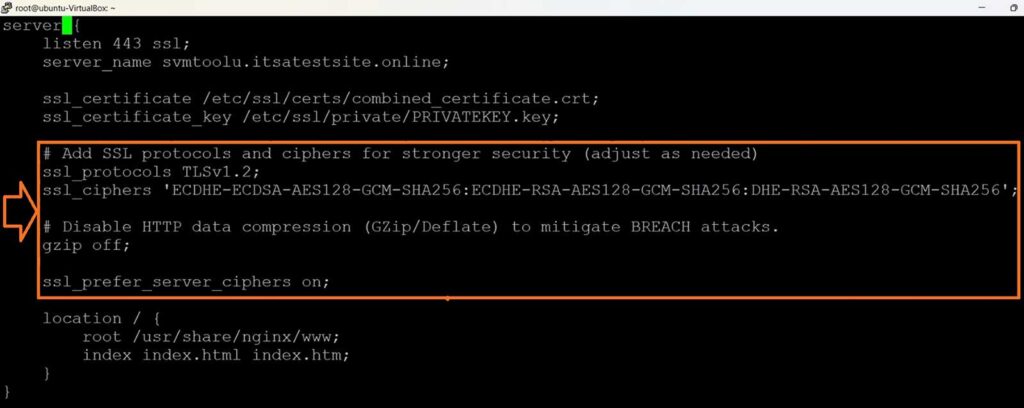
- Restart NGINX using the following command:
sudo service nginx restart Older Distributions
For unsupported distributions, first manually update OpenSSL to ensure it’s up to date and secure:
wget https://www.openssl.org/source/openssl-1.0.1g.tar.gz
tar -xzf openssl-1.0.1g.tar.gz && cd openssl-1.0.1g
./config && make && sudo make install
sudo mv /usr/bin/openssl /usr/bin/openssl.old
sudo ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
sudo apt-get install --reinstall libssl1.0.0 -y
sudo reboot3. Windows Server with IIS
- Download and run IIS Crypto:
- Download from IIS Crypto’s website and run it as an administrator.
- Disable insecure cryptography:
- Click Best Practices to turn off SSL 3.0, TLS 1.0, and 1.1, and to turn on TLS 1.2 and select secure ciphers.
- Customize the server’s supported protocols, ciphers, and other settings (optional):
- Adjust the selected protocols and ciphers as needed, prioritizing stronger ciphers like AES256-GCM.
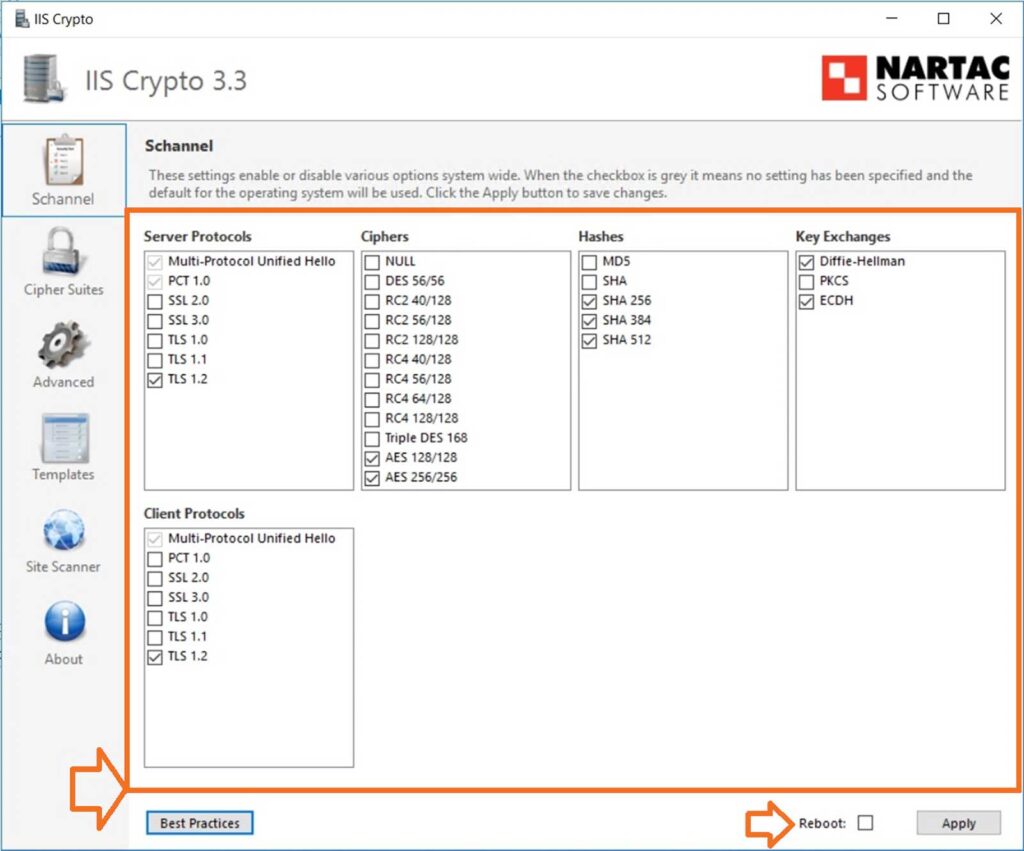
- Save and reboot your server:
- Click Apply to save the settings and reboot the server to apply the changes.
Verification Report: Ensure All Servers Are Secured Against SSL Vulnerabilities
After applying the security measures, scans with CertPanel SSL Monitor SSL vulnerability scanner tool confirm that all servers — CentOS, Ubuntu, and Windows IIS — are now vulnerability free.

Why Use CertPanel SSL Scanner?
CertPanel SSL Scanner is an easy-to-use, automated way to manage your SSL vulnerabilities. Its features are as follows:
- Full SSL Online Scanning: Find weak ciphers, outdated protocols, and certificate problems.
- Detailed Reports: Offer actionable advice for how to fix those vulnerabilities.
- Real-Time Alerts: Keep you abreast of new ones.
Sign up now for your free trial of CertPanel SSL Monitor and gain control over your SSL security today.
Final Takeaways
Managing SSL vulnerabilities is essential to protecting your website and its users from many cybersecurity threats. You will be able to ensure robust configurations for your server by using tools such as CertPanel SSL Monitor’s SSL vulnerability scanner, along with industry best practices.
Protect your site today!Sign up for CertPanel SSL Monitor today to secure your website and server against 110+ SSL vulnerabilities.