The POODLE Attack, which stands for Padding Oracle on Downgraded Legacy Encryption Attack, is a well-known vulnerability in systems that support SSL 3.0 (CVE-2014-3566). Despite being deprecated, many modern systems continue to enable SSL 3.0 for the sake of compatibility with legacy systems, making them vulnerable to POODLE.
In this guide, you’ll learn:
- What the SSL POODLE Attack entails
- How to detect the POODLE vulnerability using CertPanel SSL Monitor.
- Ways to fix POODLE by disabling SSL 3.0 on NGINX, Apache, and Windows Server (IIS).
- How CertPanel SSL Monitor’s features enable you to easily manage and monitor your SSL security.
What Is the SSL POODLE Attack?
The POODLE attack is a cryptographic vulnerability that targets a weakness in the cipher block chaining (CBC) padding process used in SSL 3.0 encryption. It starts with a TLS protocol downgrade attack that results in the target server switching to using the weaker SSL 3.0 protocol.
By exploiting this downgrade, a man-in-the-middle attacker can decrypt secure HTTPS traffic between a user and a website, resulting in unauthorized access, theft, and modifications of data in transit.
This makes it critical to disable SSL 3.0 support on your servers. So, how do you fix it?
Mitigation: Upgrade your servers to use TLS 1.2 or TLS 1.3 only, as neither protocol is susceptible to POODLE.
How to Detect SSL POODLE with CertPanel SSL Monitor
CertPanel SSL Monitor is a website security tool that makes it easy to detect and deal with vulnerabilities like CVE-2014-3566 exploit (i.e., POODLE). Its continuous monitoring and alerting capabilities for 110+ website and SSL/TLS vulnerabilities go a long way in improving the security of your site.
Here is how you can detect the SSL POODLE vulnerability using the CertPanel SSL Monitor feature:
- Log in to CertPanel. Once logged in, navigate to the Featured Products section of the CertPanel dashboard and select Activate SSL Monitor. Enter your domain name and hit Place Order.

- Launch SSL Monitor. Now, you’ll be able to access CertPanel SSL Monitor for that domain from your main dashboard screen, under Assets.
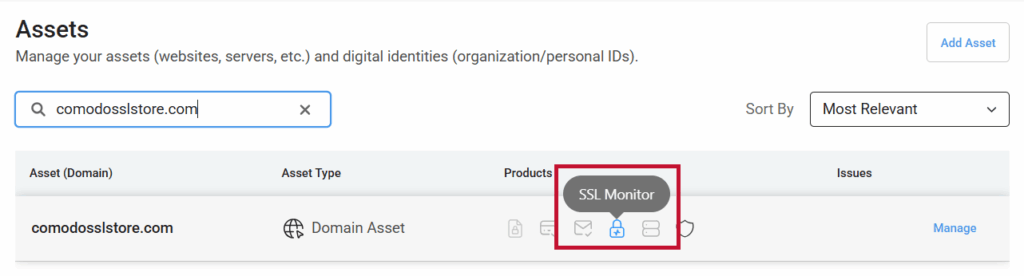
- Generate an SSL scan. CertPanel SSL Monitor enables you to automatically scan your website for 110+ issues, including the POODLE protocol vulnerability.
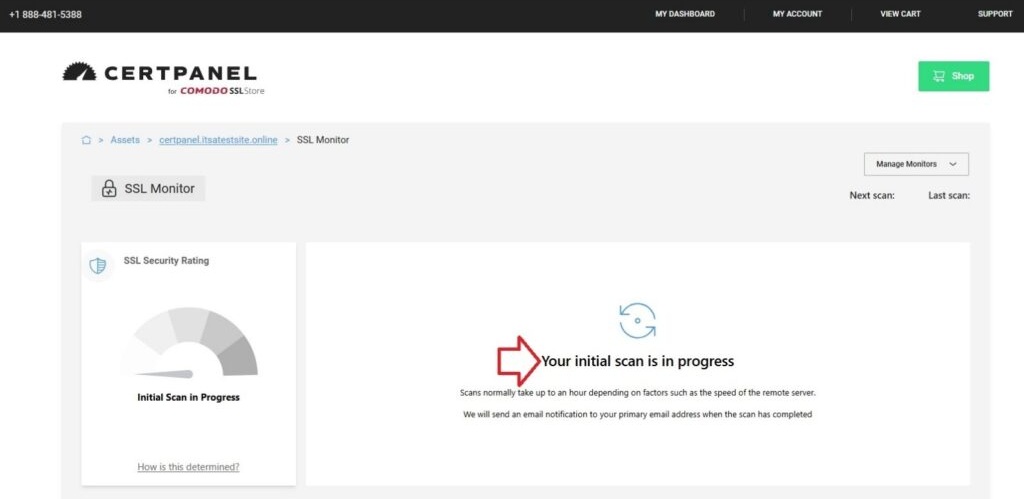
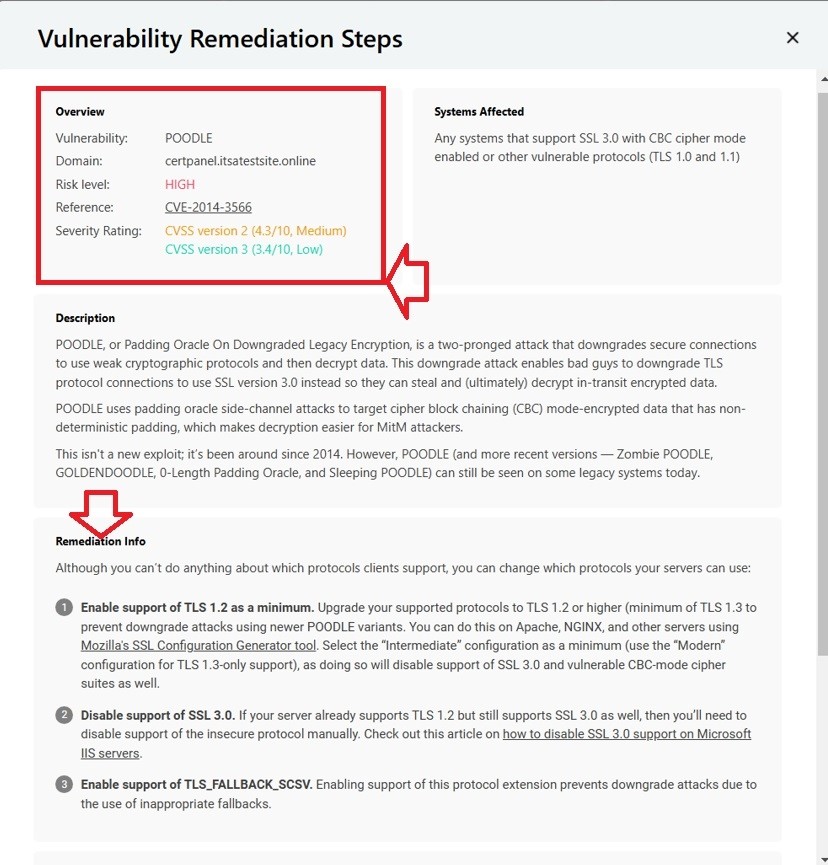
- Review the vulnerabilities and fix them. The CertPanel SSL Monitor scan results will highlight vulnerabilities and offer recommendations for how to fix them. If SSL 3.0 shows as enabled, simply follow the instructions that detail how to disable the protocol on your server.
How to Fix the POODLE Attack SSL Vulnerability on Different Servers
1. Disable SSL 3.0 on Apache
To eliminate the POODLE vulnerability on Apache, you’ll need to set your minimum protocol to TLS 1.2 in the server’s SSL configuration settings. The specific file paths you’ll use will vary based on your specific Linux distribution. For example, you’ll use /etc/apache2 for Ubuntu and Debian or /etc/httpd/ for CentOS, Rocky Linux, and RHEL.
For this example, we’ll show you how to check and change your Apache server’s SSL/TLS protocols in CentOS:
- Check your current SSL protocol configuration:
grep -Ri “SSLProtocol” /etc/httpd/- Open the SSL configuration file:
sudo vim /etc/httpd/conf.d/ssl.conf- Change or add the SSLProtocol directive in the virtual host. This is where you’ll disable the use of weak protocols (including SSL 3.0). Here’s how to do it:
<VirtualHost *:443>
ServerName yourdomain.com
SSLEngine on
# Protocols — Disable insecure protocols and use only TLS 1.2 and 1.3
SSLProtocol -all +TLSv1.2 +TLS1.3
</virtualHost>- Save the file and restart your Apache server. (Note: This command may differ slightly based on your Linux distro.)
sudo systemctl restart httpd- Run a scan of your domain using CertPanel SSL Monitor. This will provide assurance that SSL 3.0 was successfully disabled.
2. Disable SSL 3.0 on NGINX
To prevent a POODLE attack on your NGINX server, disable SSL 3.0 and enable only TLS 1.2 or higher. The specific file paths you’ll use will vary based on the server’s Linux distribution. For example, to do this in Ubuntu or Debian:
- Check your current SSL/TLS protocol configurations:
sudo grep -Ri “ssl_protocols” /etc/nginx/sites-available- Open the virtual host configuration file:
sudo vim /etc/nginx/sites-available/default- Set the ssl_protocols directive to include only the TLS 1.2 protocol or higher:
ssl_protocols TLSv1.2 TLSv1.3;- Save the file and restart your NGINX server:
sudo service nginx restart- Run a new scan in CertPanel SSL Monitor. This will allow you to verify that SSL 3.0 is disabled and confirm your server’s improved security posture

3. Disable SSL 3.0 on Windows Server (IIS)
To fix the POODLE vulnerability on Windows Server systems running IIS, you need to disable SSL 3.0. While this can be done manually through the Windows Registry, do so with extreme caution.
- Open the Registry Editor by entering the following command in your run bar.
regedit- Navigate to the following in the navigation tree: HKEY_LOCAL_MACHINE > System > CurrentControlSet > Control > ServiceProviders > SCHANNEL > Protocols > SSL 3.0 > Server.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server - If SSL 3.0 or the subfolder Server don’t yet exist, you’ll need to create one or both:
- To create the protocol entry: right-click on Protocols and select New > Key from the drop-down menu. Name this entry SSL 3.0.
- To create the Server key: right-click on SSL 3.0 and select New > Key and name the entry Server.
- Disable SSL 3.0 on the server.
- Right-click on the new Server key and select New > DWORD (32-bit) Value.
- Enter Enabled as the value and set the value data as 0, which disables the protocol, before clicking OK.
- Restart your IIS server to apply the change. Do this by entering the following command below. (Alternatively, if you don’t feel comfortable editing the registry directly, you can use a tool like IIS Crypto.):
iisreset- Verify your changes are successful. Use CertPanel SSL Monitor to scan your server and confirm that SSL 3.0 is disabled and the POODLE vulnerability is resolved.
CertPanel SSL Monitor Streamlines Vulnerability Management & Prevents POODLE Attacks
CertPanel SSL Monitor is a practical and affordable tool for non-enterprise organizations. This tool enables small businesses to monitor their websites for any SSL/TLS-related vulnerabilities and be alerted to dozens of security-related issues:
- Constant scanning for weak protocols
- Instant alerts when SSL 3.0 or similar risks are detected
- Detailed recommendations with guided fix steps
- Historical reports for audits
The SSL POODLE attack (CVE-2014-3566) is a vulnerability that can compromise encrypted data on servers still supporting SSL 3.0. By setting TLS 1.2 as the minimum protocol version and using CertPanel SSL Monitor to keep an eye on things, you can proactively secure your site and provide a safer experience for users.
Ensuring strong SSL/TLS protocols protects your website from outdated encryption vulnerabilities like POODLE, reinforcing trust and reliability.
Start scanning now with CertPanel SSL Monitor to identify and fix SSL issues before they impact your users.