The Factoring RSA Export Keys (FREAK) vulnerability, also known as CVE-2015-0204, is a major SSL/TLS security problem for servers and clients that support outdated protocols and ciphers. In a nutshell, the FREAK Attack enables attackers to force systems to use vulnerable “export cipher suites” and small key pairs. This allows them to intercept and decrypt (what should have been) secure communications.
This article offers insights into the FREAK vulnerability, shows an example of a hacked vulnerable server, and explains how you can identify and mitigate the FREAK vulnerability exploit to protect your web servers. In particular, we look at how CertPanel SSL Monitor can help spot and fix this issue.
TL;DR: Key Facts About the FREAK Attack
- Common Vulnerability and Exposures (CVE) ID: CVE-2015-0204
- What the FREAK Attack Does: Allows attackers to intercept and decrypt HTTPS traffic by forcing servers and clients to use intentionally insecure “export-grade” cryptography.
- How It Works: In this downgrade attack, threat actors exploit a vulnerability that forces SSL/TLS connections to use weak cipher suites and 40- or 56-bit cryptographic keys.
- Affected Systems: Primarily affects servers and clients using vulnerable SSL/TLS configurations, particularly those that support export-grade RSA keys.
The CVE-2015-0204 Exploit (FREAK Vulnerability) Explained
Although it’s not new, the FREAK Attack still poses a major threat to vulnerable legacy systems and clients. (Reason #892,000 for why you should not rely on old, unsupported systems.) This vulnerability, which was discovered in 2015, triggers the use of insecure cipher suites from the 90s. This cryptographic downgrade attack puts clients and servers that support these RSA export-grade keys at risk of compromise or exposure.
So, why are these cipher suites and keys so weak? They were designed that way to adhere to regulations surrounding the export of cryptographic technologies to foreign entities. These keys were made intentionally weak to enable U.S. security and intelligence organizations to decrypt and read confidential data. Unfortunately, bad guys know this and can exploit vulnerabilities to trick a server and client into using them. This lets them read secret messages between the server and client.
How to Detect the FREAK Vulnerability Using Manual or Automated Methods
You can manually check to see which ciphers or cipher suites your server supports using several tools. For our example, we’ll use OpenSSL.
Manually Check Your Domain’s Supported Cipher Suites in OpenSSL
Enter the following OpenSSL directives. (Note: Be sure to replace the generic values with your unique domain and the specific cipher suits you want to check.)
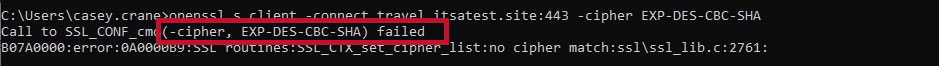
openssl s_client -connect <hostname>:<port> -cipher <ciphersuite-name> For example, if we want to check to see whether the export cipher suits “EXP-DES-CBC-SHA” is supported on our test server, we can use this command:
openssl s_client -connect travel.itsatest.site:443 -cipher EXP-DES-CBC-SHAWondering why we used -cipher instead of -ciphersuites? It’s because –cipher works for TLS 1.2 and earlier cipher suites, whereas -ciphersuites only works with TLS 1.3 cipher suites, which follow a different format/naming convention.
Here’s a quick look at what you’re likely to see:
Don’t have time to run every relevant cipher suite? Then you’re in for some good news, as there’s another way…
Automatically Scan for the FREAK Vulnerability Exploit Using SSL Monitor
Using CertPanel’s SSL Monitor, you can scan your server to identify if it’s susceptible to the FREAK Attack (and 110+ other vulnerabilities). SSL Monitor quickly identifies weak protocol configurations, misconfigurations, and weak cryptography (including support for export-grade cipher suites and RSA keys).
Here’s how you can check your domain for vulnerable cipher suites that bad guys can use to launch a FREAK Attack.
- Access SSL Monitor: Go to CertPanel and activate the SSL Monitor feature.

- Enter your domain or IP address: Input the domain name or IP address of the server you want to scan for vulnerabilities.
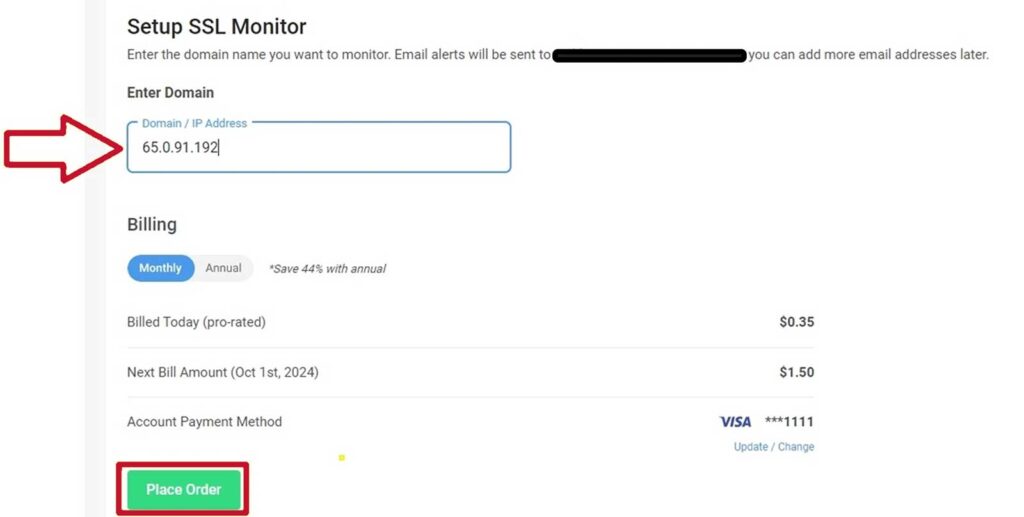
- Start the scan: Click Go to SSL Monitor to initiate a scan of your domain or IP address. This process analyzes your SSL/TLS configuration and reports any weaknesses.

- Review your individual report: Check the results for any mentions of weak or export-grade RSA keys and implement the remediation steps.

How to Mitigate the FREAK Vulnerability to Prevent Exploitation Attacks
For starters, ensure your server and OpenSSL client are up to date. If not, update or patch them now so bad guys can’t exploit these outdated, vulnerable systems.
If you haven’t already done so, ensure your server is set to support TLS 1.2 as the minimum security protocol. (Ideally, TLS 1.3.)
Disable Export Ciphers in Apache and NGINX
To secure your server against FREAK, you need to disable support for export-grade RSA keys and ensure your server is configured to use strong encryption standards. Below are the steps to remove export ciphers for both Apache and NGINX Linux configurations:
Step 1: Open the Relevant Configuration File on Your Server
- Apache users: You’ll find this file at /etc/httpd/conf.d/ssl.conf or /etc/apache2/sites-enabled/default-ssl.conf.
- NGINX users: You can locate this config file at /etc/nginx/nginx.conf or in the sites-available folder.
Step 2: Change the Cipher Suite Settings to Remove Weak Ciphers
- Apache users: Locate the SSLCipherSuite directive and modify or update it to:
SSLCipherSuite HIGH:!aNULL:!MD5:!EXPORT 
- NGINX users: Modify or update the ssl_ciphers directive to say the following:
ssl_ciphers HIGH:!aNULL:!MD5:!EXPORT; 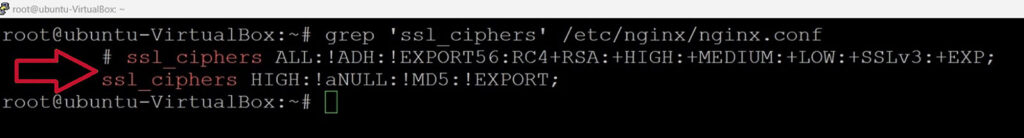
Step 3: Save the Changes and Restart Your Web Server to Update the New Settings
- For Apache:
sudo service apache2 restart - For NGINX:
sudo service nginx restart Step 4: Re-Run the Server Vulnerability Scanner
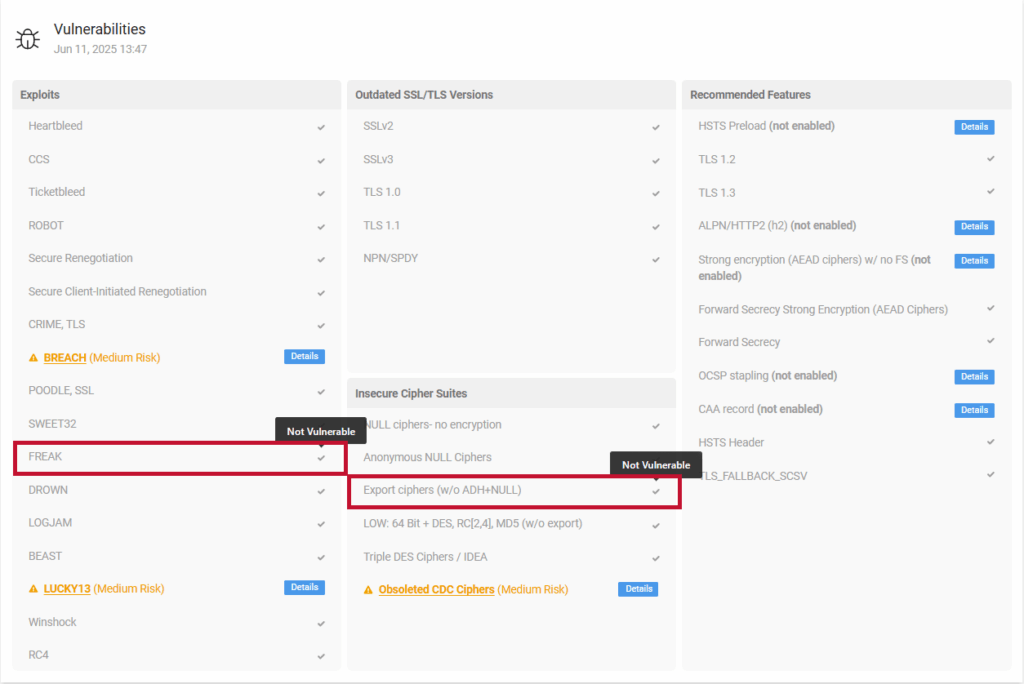
Check whether your changes have resolved the FREAK vulnerability.
Final Takeaways
The FREAK vulnerability exploit has a significant impact on SSL/TLS security for vulnerable servers and clients, making encrypted communications less secure. Tools like CertPanel SSL Monitor help organizations spot these issues and act quickly to protect their servers. Follow the outlined mitigation steps for your specific server to ensure your environment is protected against FREAK Attacks.
For a comprehensive scan of your web server’s security, try CertPanel’s SSL Monitor today and keep your site safe from known vulnerabilities like FREAK, Heartbleed, and more.